The main defense against wireless leechers is securing your wireless router. Even though most wireless routers from ISPs come with long passwords, someone can still gain access by simply copying the password printed on your wireless router, since most people don’t change the default password set by their ISP. If you have a router that you bought on your own, no one will be able to use the password written on the router unless you don’t change the default password. We’ll talk about all this below. Let’s first talk about how to detect wireless leechers.
Detect Unauthorized Wireless Connections
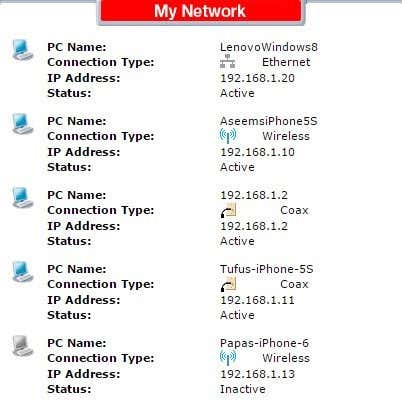
There are basically two ways to go about detecting all the devices connected to your wireless router: either check on the router itself or use a device already connected to the network to scan the entire network. I prefer the latter method because it’s less complicated, however, I will mention both ways. The first step is to connect to your wireless router from your web browser. In order to do that, you have to type in the IP address for your router. If you don’t know it, read my post on determining the IP of your wireless router. Once you have that, you’ll need to login using the username and password. If you don’t remember the password or you never changed the default password, that’s a problem. In either of these cases, I recommend resetting your wireless router to factory default settings and starting from scratch. It may sound like a monumental task, but it’s really not. First, read my post on resetting your wireless router, which is fairly easy to do. Next, don’t worry if you don’t have the paperwork for your router anymore because you can either find the default password on the router itself or you can find default router passwords online. Once you are able to log into your router, you can check what IP addresses have been allocated on the network. Usually, this information is located somewhere on the main page and can be called something like Devices, My Network, IP Address Allocation, Attached Devices, Wireless Status, Connected Devices, DHCP Clients Table, etc. It really depends on the router you have, but you should see a list like the one shown below.
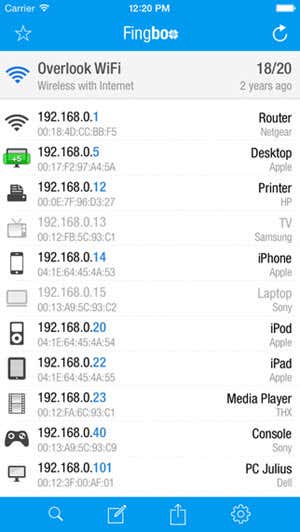
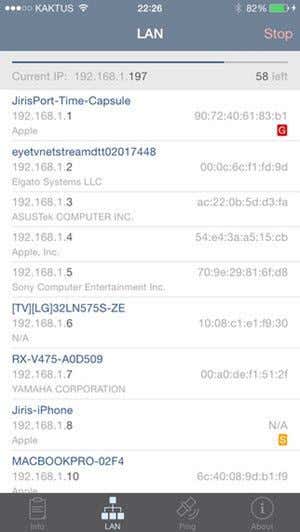
Most new routers will also show you the name of the devices, so it’s easy to tell if the device is a phone, tablet, printer, IP camera, NAS, streaming device, laptop or computer. If you can’t figure out what device is associated with an IP address, you can always try to paste that IP into your web browser and see if it loads a web page. Some printers, camera, etc. will have their own web interfaces that you can connect to via the browser. If all of that is too complicated, another method to find connected clients is to use a smartphone app. For Apple devices, I recommend Net Analyzer Lite and Fing Network Scanner. Fing is also available in the Google Play Store.
These apps are actually better than going directly to the router most of the time because they can give you more information about the device. Fing can even figure out if you have a console on your network, which is pretty cool. Now it should be pretty easy to find a device that is not supposed to be connected to your network. If this is the case, what can you do? Keep reading to find out how to secure your wireless network.
Secure Wireless Network
The first step you should take if you think your network has been compromised is to completely reset your router as mentioned earlier or buy a new router if the current one is old. If someone was able to connect to your wireless router, they could have also compromised the router and may be able to monitor all activity on the network. The next step is to log into your router and to immediately change the default login for the router. Many people assume that setting a strong WiFi password is all they need, but this is not case. It is true that in order for someone to log into your router, they first have to be connected to the wireless network. However, there are many times when you have guests who you cannot trust fully that need to connect to your wireless network for a short time.
Router Admin
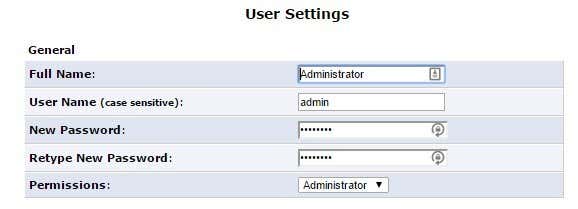
Once connected, if they are the hacker type, they might try connect to your router and try the default username and password to log in. If you never changed it, they now can access your router and have full control over your WiFi network. So change the router login password immediately.
If you can change the username also, go ahead and do that. Admin is the absolute most common username on routers and changing it makes it much harder for someone to gain access to your router. If you have a wireless router from an ISP, the username and password for the router admin interface is also printed right on the device, so make sure to change it from the default values. You’ll have to poke around the various setting and configuration pages as these options are located in different places for different vendors. Now that you have changed the router login info, the next step is to setup the wireless security.
WPA/WPA2
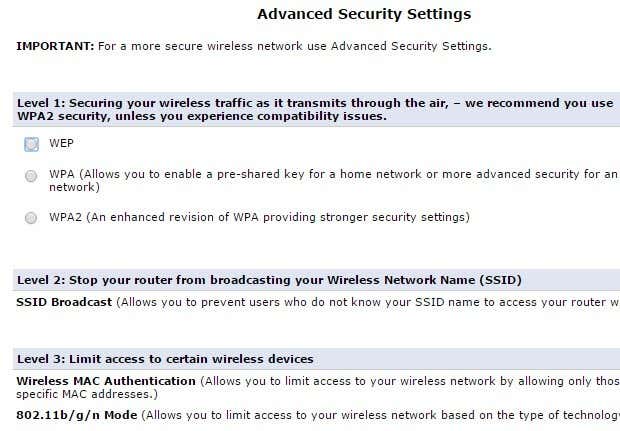
There are three main ways to secure your router at this point: choosing between WEP, WPA, and WPA2 encryption, disabling SSID broadcast and enabling wireless MAC authentication. I firmly believe you really only need to use WPA2 encryption with a long key to be very secure, but some people like to take extra precautions and it could be worth the extra effort if you have very sensitive information stored on your devices.
Some routers make this really easy for you, like the Verizon FIOS router advanced security settings page shown above. You should only use WPA2, if possible. WEP is very insecure and WPA can be cracked fairly easily. If you have devices on your network that cannot connect once you setup WPA2, then you should pick the option that has WPA + WPA2 Personal. Make sure you choose a long password. Note that it doesn’t have to be a bunch of random numbers, symbols, or letters to be secure. A strong password just has to be a long passphrase. If you’ve followed the steps above, resetting your router, configuring the admin password and using WPA2, you can pretty much be certain that anyone previously connected to your wireless network is now disconnected. If you want to go further, you can read my post on disabling SSID broadcast, but it really doesn’t make your network much more secure. Enabling MAC address filtering will make your network more secure, but it makes everything a lot less convenient. Every time you want to connect a new device to your network, you’ll have to find the MAC address for the device, log into your router and add that to the filtering list. In conclusion, if you suspect unusual activity on your network, you should immediately follow the steps outlined above. There are chances someone may be monitoring your computer if they are connected to your network, so it’s better to be safe than sorry. If you have any questions, post a comment. Enjoy!